(20180226 – This post has been amended to reflect changes in pfSense version 2.4.2 — iceflatline)
This post will describe how to install and perform initial configuration of pfSense for use in a home network. pfSense (i.e., “making sense of packet filtering”) is a customized version of FreeBSD tailored specifically for use as a perimeter firewall and router, and managed almost entirely from a web-based GUI (“webConfigurator”). In addition to being a firewall and router, pfSense includes a long list of other features, as well as a package system allowing its capabilities to be expanded even further. pfSense is free and open source and its source code is released under the BSD license.
So, let’s get started…
Hardware Considerations
- Minimum requirements
The minimum hardware requirements for pfSense include a 500 MHz CPU, 512 MB of system RAM, 1 GB hard drive, and a minimum of two Network Interface Controllers (NIC). You’ll also need a CD-ROM drive or bootable USB drive in order to install pfSense to the hard drive. These requirements are extremely modest, but unless your data throughput requirements are fairly small, you’re likely going to want to use hardware offering a little better performance. Since a major contributor to throughput performance is the system’s CPU, let’s start there. pfSense published guidelines for CPU sizing recommends the following:
- 10-20 Mbps – a modern (less than 4 year old) Intel or AMD CPU clocked at at least 500MHz
- 21-50 Mbps – a modern 1.0 GHz Intel or AMD CPU
- 51-200 Mbps – No less than a modern Intel or AMD CPU clocked at 2.0 GHz. Server class hardware with PCI-e network adapters, or newer desktop hardware with PCI-e network adapters
- 201-500 Mbps – server class hardware with PCI-X or PCI-e network adapters, or newer desktop hardware with PCI-e network adapters. No less than 2.0 GHz CPU
- 501+ Mbps – Multiple cores at > 2.0GHz are required. Server class hardware with PCI-e network adapters
Your choice of NICs will also have a significant impact on reliability and throughput performance. Low cost NICs, notwithstanding the potential long term reliability concerns, tend to rely much more on the system CPU to process segments and packets compared to their higher priced counterparts. Consequently, the better the NIC, the better the throughput performance you can expect from a given CPU. In short, don’t be too frugal when it comes to the NICs you use. Intel NICs are well supported under FreeBSD and always a good choice. If possible use discreet NICs rather than the on-board ones featured on many motherboards.
You should also ensure you have enough system memory. The pfSense hardware requirements recommend 1 GB of RAM. Whether or not you’ll need more will depend largely on how you decide to operate pfSense. Some of the add-on packages for example will increase RAM requirements significantly. Another factor to keep in mind when considering memory requirements is the number of active network connections. pfSense keeps track of active connections using a state table. The default state table size is 10,000 entries, each requiring ~1 KB of RAM or ~10 MB in total – likely more than adequate for handling most home networks. But, if you require a significantly larger state table, keep system memory requirements in mind.
- Compatibility
pfSense is purportedly compatible with any hardware supported by the FreeBSD version a particular pfSense build is based upon. pfSense version 2.4.2 for example is based upon FreeBSD 11.1-RELEASE. It’s always a good idea, however, to check the hardware you’re planning to use against the information contained in the FreeBSD 11.1-RELEASE hardware notes and the hardware compatibility section of the Frequently Asked Questions for FreeBSD 10.x and 11.x. The pfSense forums are another good resource, useful for gleaning the hardware compatibility experiences of others.
Installation
Performing a full installation of pfSense is a straight forward; however, before you get started there are a couple of preliminary steps I recommend. First, make a note of the Media Access Control (“MAC”) address for each NIC you’re installing in the system as well as its physical location in the motherboard. If your memory is as bad as mine, this will save you from wondering later “…now which NIC did I assign as the LAN interface?…” Second, disconnect the NICs from any LAN and WAN devices until you have the box up and running and configured to your requirements. Finally, if you have other hard drives in the system I recommend disconnecting them until the installation is complete so as to not accidentally install to the wrong drive.
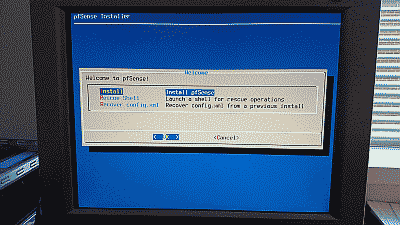
Download a copy of the pfSense installer and burn it to a CD or place it on a bootable USB drive. After booting the system using the CD or USB drive and accepting the copyright and distribution notice, you’ll arrive at the initial installation screen (See Figure 1).
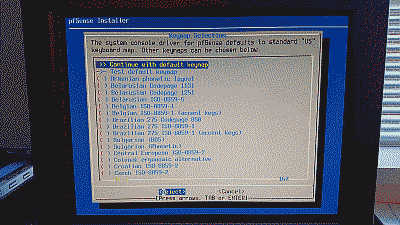
Select “OK” to continue. The pfSense installer will ask whether it should continue with the default U.S. keyboard key map or use a different one (See Figure 2).
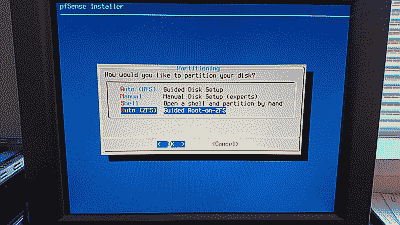
After configuring the keymap, the installer will ask and whether it should partition the hard drive using the UFS or ZFS file system. I advise using ZFS if possible (See Figure 3).
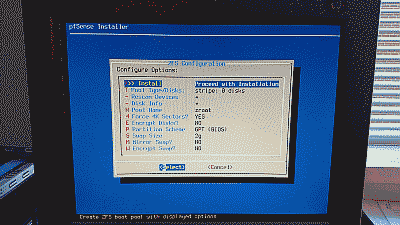
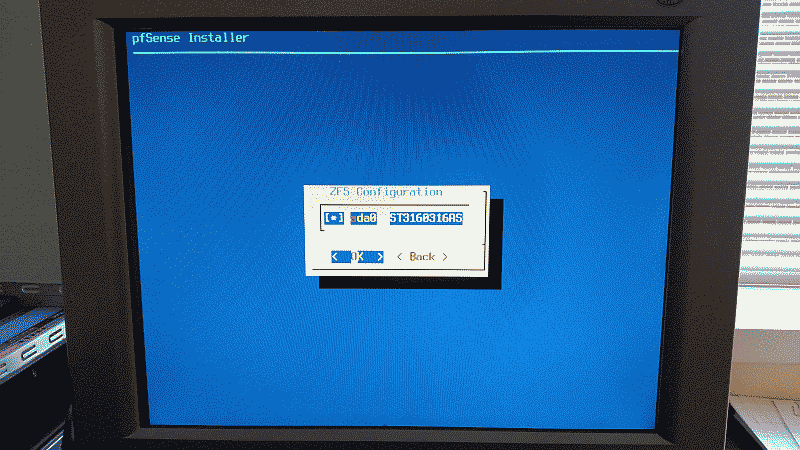
Unless your requirements call for something different, the default ZFS configuration options will work just fine (See Figure 4).
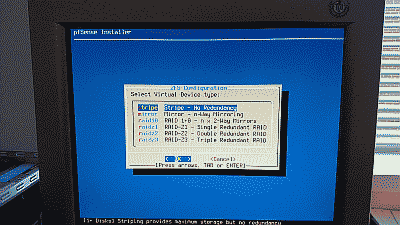
Next, the installer will ask you select a ZFS virtual device type. The steps in this post assume you’ll be installing pfSense on a single hard drive. The stripe option is the correct choice in this case. If your requirements call for installing pfSense using two or more hard drives then you have the option of selecting a mirror or one of the raidz virtual devices types (See Figure 5).
The installer will then ask you to confirm the choice of hard drives (See Figure 6).
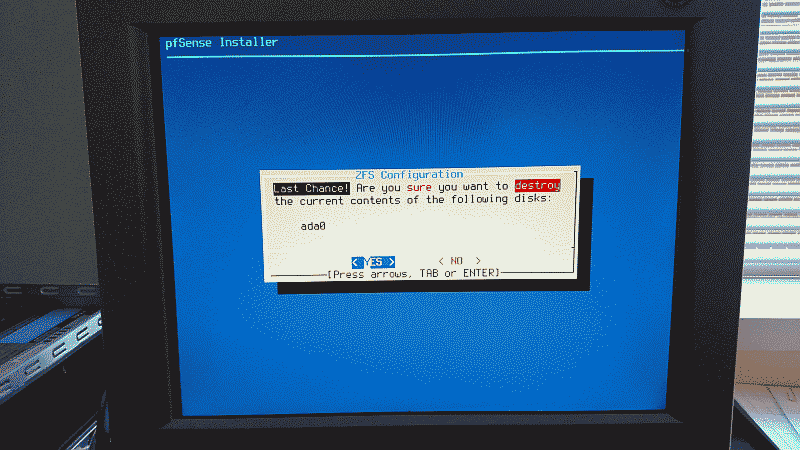
Finally, the installer will offer one last chance before destroying any previous content contained on the hard drive and continuing with the installation. If you’re satisfied with your configuration choices select “YES” to proceed (See Figure 7).
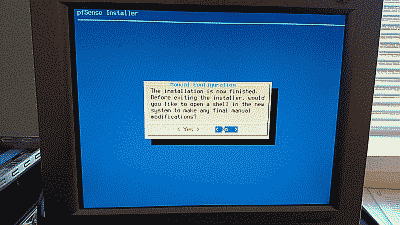
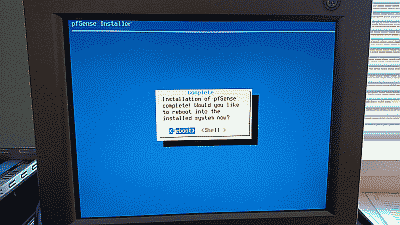
After the installer finishes the installation you’ll be offer the opportunity to open a shell session in order to make any modifications manually (See Figure 9).
If no further changes are required select “No” the installation will be complete and the system will ask to be rebooted (See Figure 9).
Configuration
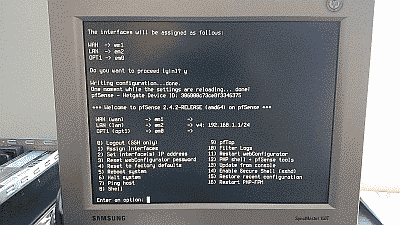
After pfSense is installed and the system rebooted, you’ll arrive at the pfSense console menu (See Figure 10).
Note that in this example pfSense has chosen the NIC assigned the device name em1 as the WAN interface, and em2 as the LAN interface (I have a third NIC in this system, which is why you see an em0 device). If you’d like to reassign these interfaces or simply want to know which MAC address belongs to each NIC, then select “Assign Interfaces” (menu option 1). Note also that pfSense initially assigns the LAN interface the default static IPv4 address of 192.168.1.1, and configures the WAN interface to use DHCP so you will not see an IP address assigned to that interface.
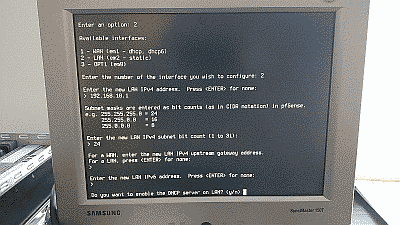
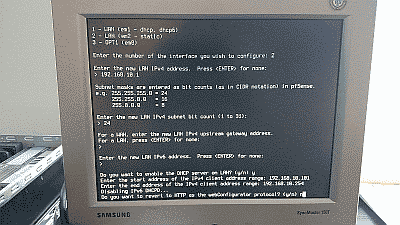
Select “Set interface(s) IP address” (menu option 2) to configure pfSense’s LAN interface IPv4 address to one that will fall within the subnet you plan to use for your network. In this example we’ve configured the IPv4 address to 192.168.10.1, assuming that the subnet will be 192.168.10.0/24.
This menu option also allows you to activate pfSense’s DHCP server and define a range of IPv4 addresses for the server to use. In this example we’ve configured the DHCP address range to be 192.168.10.101 to 192.168.10.254 (See Figure 12)
Once the IPv4 address and DHCP server are configured, you’ll be asked if I want to revert to HTTP as the webConfigurator protocol (as opposed to using to using HTTPS). I recommend declining this option to improve login security. After these steps are completed you will be returned to the console menu.
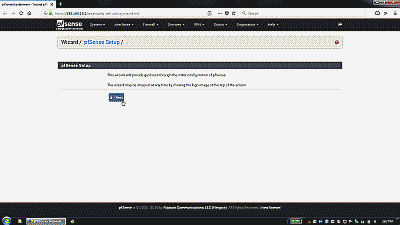
Now, connect to the LAN interface, fire up your web browser, and navigate to IPv4 address you assign to the LAN interface to access the pfSense webConfigurator. The webConfigurator login is password protected – the default login is admin and the password is pfsense. The first time you login to a new installation of pfSense, you ne greeted with the pfSense setup wizard to perform an initial configuration (See Figure 13).
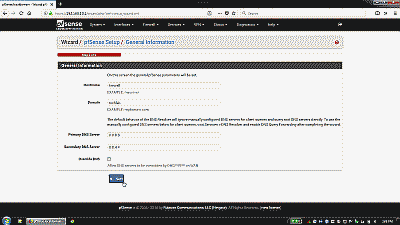
The setup wizard starts by asking you to define the hostname for your new pfSense system, the domain where it will reside, and primary and secondary DNS servers. You can use any hostname you’d like but be aware of the following constraints: the hostname you choose must start with a letter, and after that contain only letters, numbers or a hyphen (e.g., “firewall” or “firewall-1”). The “Domain” field can be filled in with any fully qualified domain (e.g., “mysite.org”) or a name of your choice (e.g., “homenet”). The hostname and domain fields are combined to create the fully qualified domain name of your pfSense box (e.g., “firewall.mysite.org” or “firewall.homenet”). If your service provider provisions your service using DHCP, then the DNS fields will be likely be filled in automatically when you connect to your provider. If you plan to use a static WAN IP address, or simply prefer to use alternative DNS providers, then you should provide at least a primary DNS address at this point (See Figure 14).
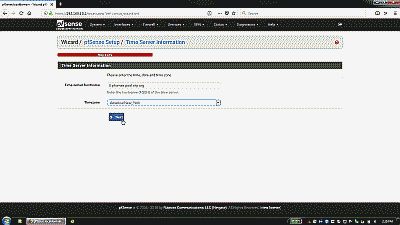
The next wizard screen is where a time server hostname and timezone are defined. I recommend using the default host 0.pfsense.pool.ntp.org, which results in a random server from a pool of known good NTP servers to be chosen automatically (See Figure 15).
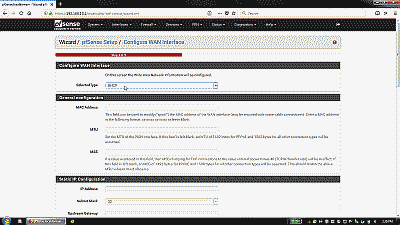
Next, you’ll be taken to the WAN section of the setup wizard. If your service provider provisions your service using DHCP, then you simply need to select “DHCP” from drop-down list, otherwise chose the appropriate service type. The “MAC Address” field under “General configuration” can be used to enter a MAC address that will pose as the MAC address of your WAN interface NIC. The “Block RFC1918 Private Networks” and “Block bogon networks” sections are selected by default in order to block invalid traffic from entering your network. The remaining sections in this portion of the setup wizard are specific to WAN service type chosen (See Figure 16)
After the WAN section, you’ll encounter the final two sections of the setup wizard. These provide the opportunity to change, if desired, the LAN IP address as well as the default password for the admin user account. Note that this password also serves as the password for SSH access as well as the console menu (should you decide to password protect it).
At the conclusion of the setup wizard, you’ll select “Reload” and after a few moments be returned to the pfSense webConfigurator. At this point basic connection options are configured enough to allow the pfSense box to be safely connected to the service provider and LAN. However, before bringing pfSense online in your network there are a couple of optional changes to its configuration you may wish to consider.
- Disable webConfigurator login autocomplete
By default login credentials for the webConfigurator may be saved by a web browser. Navigate to System->Advanced->Admin Access and select “Disable webConfigurator login autocomplete” to disable autocomplete on the login form so that browsers will not prompt to save credentials (Note that some browsers do not respect this option). When complete, select “Save”.
- Password protect the console menu
While pfSense is managed almost entirely from its webConfigurator, it does allow some configuration management through its console menu (See Figure 10). By default, pfSense does not secure this menu, therefore, anyone who can physically connect a monitor to the pfSense machine will have root level shell access. To prevent this (or at least make it more difficult), navigate to System->Advanced->Admin Access and select “Password protect the console menu.” When complete, select “Save.” You’ll need to reboot the system for this change to take effect. Note that the user name for the console menu is always admin or root and the password will be “pfSense” by default, or the one you chose if you elected to change the default admin password when running the setup wizard. It’s also worth noting here that if you create a new user, this new user will only be allowed access to a command line prompt at the terminal, not the console menu itself, even if you add them to the system’s admins group (See System->User Manager).
- NAT Reflection mode for port forwards
By default pfSense prevents hosts within the LAN from accessing your public IP addresses. This can be inconvenient at times, particular when testing port forwarding from within the LAN. To change this, navigate to System->Advanced->Firewall & NAT and, depending on your requirements, select either “NAT + proxy” or “Pure NAT” from among the options in the drop down list under “NAT Reflection mode for port forwards”. When complete, select “Save”. A reboot is not needed when selecting this option so you can use it on an as-needed basis if desired.
- Packages
As mentioned, pfSense offers a fairly extensive package system allowing you to extend its capabilities. To find a list of packages that can be added, navigate to System->Package Manager->Available Packages to view the available software packages.
- Firewall
Setting up NAT port forwarding and firewall rules in pfSense can be a bit daunting at first. Once you get the hang of it though you’ll realize just how flexible and powerful the system is. Options for configuring port forwarding and firewall rules can be found under Firewall->NAT and Firewall->Rules respectively. I recommend setting up any port forwarding rules you may have first. Then, for each port forwarding rule, you’ll need to set up an associated firewall rule. When complete, select “Save”, then “Apply changes”.
- DHCP
Options for configuring the DHCP server on the LAN interface can be found under Services->DHCP server. If you’re deploying pfSense in a typical home network where the availability of IP addresses is not a concern, one option you may want to consider changing is the default lease time of 7200 seconds (two hours) in order to reduce the number of lease requests in the network. This is also the section where you can assign static IP addresses to hosts, if desired. For example, you may wish to assign static IP addresses to servers and network devices (managed switches, network printers, etc.), as well as to any hosts you intend to build long-term port forwarding rules for.
- UPnP
If you have game consoles like Microsoft Xbox, you know what a pain it can be at times to get them to connect reliability to services like Xbox Live through your home network gateway/firewall. A common solution is to forward the necessary ports to these devices, but what if you have more than one? If you want one or more game consoles to have reliable access to their respective services, the only real solution is to use Universal Plug and Play (UPnP). Fortunately, pfSense’s UPnP service works remarkable well. To activate it, navigate to Services->UPnP & NAT PMP and select “Enable UPnP & NAT PMP” and “Allow UPnP Port Mapping” then ensure that the LAN interface is selected under “Interfaces”. When complete, select “Save”. That’s it. Your game consoles will discover pfSense’s UPnP server and the necessary port forwarding rules will be built automatically as needed. You can check which ports have been forwarded by navigating to Status->UPnP & NAT PMP.
- Wake on LAN
The Wake on LAN in feature in pfSense allows you to instruct it to send the Wake on LAN “magic packet” to a network host you need to power up. To setup Wake on LAN, navigate to Services->Wake-on-LAN and select the “+ Add” icon. Select the LAN interface and enter the MAC addresses for the host you’d like to send magic packets to. When complete, select “Save”.
- System Logs
You may wish to have log entries arranged so that the newest entries appear first. To do that, navigate to Status->System Logs->Settings and select “Show log entries in reverse order (newest entries on top)”. When complete, select “Save”.
Remote Access
pfSense’s webConfigurator uses HTTPS and port 443 by default, and accessing it remotely is simply a matter of navigating to your WAN address. Unfortunately, many ISPs block incoming port 443 traffic. You can chose an alternate incoming TCP port by navigating to System->Advanced->Admin Access and entering the port number in the “TCP port” field. When complete, select “Save”. You will also need to create a new firewall rule under Firewall->Rules that will allow a connection on the WAN interface to pass through to pfSense’s webConfigurator server on the port you specify. At a minimum, this rule should define following parameters:
Action: Pass
Interface: WAN
TCP/IP Version: IPv4
Protocol: TCP
Destination: WAN address
Destination port range: your alternate webConfigurator port selection
Description: web admin
pfSense’s SSH server may also be enabled to allow remote access to the console menu via an SSH client. To enable the SSH server, navigate to System->Advanced and select “Enable Secure Shell”. For improved security, I recommend using an incoming port other than 22 and a key-based login instead of a password. To use a key-based login, select “Disable password login for Secure Shell (RSA/DSA key only)” and select “Save”. Then navigate to System->User Manager and paste your public key into the “Authorized SSH Keys” field. When complete, select “Save”. Note that your public SSH key is stored in /root/.ssh/authorized_keys. Should you need help generating a public/private key pair please see my post Remote Access To Your Ubuntu Server Using PuTTY, Hamachi and SSH. Don’t forget to create a new firewall rule under Firewall->Rules that will allow a connection on the WAN interface to pass through to pfSense’s SSH server should you decide to use an alternate SSH port.
Conclusion
This concludes the post on how to install and configure pfSense on your home network. pfSense isn’t hard to configure nor complicated to manage, and proves to be a nice open source package for implementing a robust and scalable perimeter firewall and router.