(20130205 – This post has been amended to reflect the most recent version of LogMeIn Hamachi — iceflatline)
This post will describe how to set up a secure virtual private network (VPN) to your Ubuntu home server using the Linux version of LogMeIn Hamachi. Once configured, you’ll be able to use secure shell (SSH) to access and manage your server from anywhere outside of your home network without the need to forward ports or make any other configuration changes on your home network gateway/router.
LogMeIn Hamachi is a hosted VPN service that is capable of establishing secure LAN-like links between computers, even if they’re behind Network Address Translation (NAT) devices. You can use it to create secure virtual networks on demand, across public or private networks. In order for LogMeIn Hamachi to work, a “mediation server,” operated by the LogMeIn, is required. The mediation server stores machine nicknames, statically allocated IPv4 (IP) addresses in the 25.x.x.x range and the associated authentication token of the user. An overview, including protocol-level details of the security architecture employed by LogMeIn can be found at LogMeIn Hamachi.
LogMeIn Hamachi provides three network types for flexibility in meeting diverse use case scenarios. They differ mainly in network topology. LogMeIn Hamachi clients can be members of any network; however, depending on the network owner’s LogMeIn Hamachi subscription, networks have the following limitations:
- Free subscription allows you to have five members in a network
- Standard subscription allows you to have 32 members in a network
- Premium subscription allows you to have 256 members in a network
- Multi-network subscription or a LogMeIn Central subscription allows you to have 256 members in all your networks
Further information regarding the subscription types can be at LogMeIn Hamachi.
SSH is a open source program for logging into a remote machine and, in most cases, for executing commands on that machine. It provides secure encrypted communications between two untrusted hosts over an insecure network. X11 connections and arbitrary TCP/IP ports can also be forwarded over the secure channel. It is intended as a replacement for rlogin, rsh and rcp, and can be used to provide other applications with a secure communication channel. To use SSH, you will need to install an SSH client on the computer you connect from (most Linux distributions and Unix variations include an SSH client), and an SSH server on the computer you connect to. The most popular open source SSH client and server are maintained by the OpenSSH project.
The versions for the software used in this post were as follows:
- LogMeIn Hamachi (Linux) v2.1.0.86-x64 (beta)
- LogMeIn Hamachi (Windows) v2.1.0.284
- OpenSSH Server v1:5.9p1-5ubuntu1
- PuTTY v0.62
- PuTTYgen v0.62
- Ubuntu server v12.04 (x64)
So, let’s get started.
Installing the SSH Server
As you may recall, the OpenSSH server is an option you have the opportunity to select when you installed and setup your Ubuntu server. If you did not select that option, you’ll need to install the OpenSSH server manually:
|
1 |
sudo apt-get install openssh-server |
If the SSH server was already installed apt will let you know, otherwise the installation will proceed. When complete, the SSH server daemon will start automatically. To check to make sure it’s running, use the following command:
|
1 |
ps -ax | grep sshd |
Install and Configure LogMeIn Hamachi on the Ubuntu Server
The LogMeIn Hamachi Linux client comes as a single executable binary compiled for the platform of your choice. This binary includes the Hamachi daemon, the control application, and the setup utility. However, before we can successfully install LogMeIn Hamachi on our Ubuntu Server we must first install the Linux Standard Base (LSB). LSB is a standard Linux core system that some third-party applications written for Linux, like LogMeIn Hamachi, use for successful implementation across a variety of distributions:
|
1 |
sudo apt-get install lsb |
With that dependency out of the way, let’s download the 64-bit Linux version of LogMeIn Hamachi to our Ubuntu server.
Then install it:
|
1 2 3 |
tar -zxvf logmein-hamachi-* cd logmein-hamachi-* sudo ./install.sh |
After LogMeIn Hamachi is installed it will start up as a background process (daemon) automatically. However, you can stop, start or restart the Hamachi daemon manually from the command line with the following commands:
|
1 2 3 4 5 |
sudo /etc/init.d/logmein-hamachi stop sudo /etc/init.d/logmein-hamachi start sudo /etc/init.d/logmein-hamachi restart |
When the Hamachi daemon is run for the first time it stays offline. Let’s bring it online:
|
1 |
sudo hamachi login |
You can change its status back to offline at any time using the following command:
|
1 |
sudo hamachi logout |
Note that the daemon remembers its state if the Ubuntu server it is shutdown or if shutdown using the sudo /etc/init.d/logmein-hamachi stop command. So if its state was online, it will automatically go online when started next time. If it was offline, it will stay offline.
Next, let’s create a nickname for our Ubuntu server so that we can identify it easily from a remote client machine:
|
1 |
sudo hamachi set-nick <your_nickname> |
Now, let’s create our LogMeIn Hamachi network. In this step you’ll need to enter a unique name for your network as well as a password for it. If your network name is already in use you’ll need to keep trying until you select one that’s unique. If you’ve previously setup a LogMeIn Hamachi network and want to simply add your server to it, then substitute join for create in the following command:
|
1 |
sudo hamachi create <your_network_name> <your_network_password> |
That’s it. Your LogMeIn Hamachi VPN should be up and running with your Ubuntu server added as one of its member hosts. You can display the status of LogMeIn Hamachi at any time by running the command sudo hamachi without any arguments. To display a full list of all the LogMeIn Hamachi command options, use sudo hamachi -h.
Install and Configure LogMeIn Hamachi on a Linux Client
Now that we’ve installed LogMeIn Hamachi on our Ubuntu Server and created a secure VPN, it’s time to install LogMeIn Hamachi on any Linux-based machines you’d like to use to access your server remotely. You can follow the steps explained above for the Ubuntu server in order to download and install LogMeIn Hamachi on your Linux macbine. Once installed, bring the logmein-hamachi daemon online:
|
1 |
sudo hamachi login |
Create a nickname for your remote client machine:
|
1 |
sudo hamachi set-nick <your_nickname> |
Then join the network you created at the server:
|
1 |
sudo hamachi join <your_network_name> <your_network_password> |
Let’s check to make sure we can see our Ubuntu server on our LogMeIn Hamachi VPN. The following command will your networks (and their hosts) that you are a member of:
|
1 |
sudo hamachi list |
Assuming that LogMeIn Hamachi is running on your Ubuntu server, you should see the nickname you created for the Ubuntu server listed, as well as the IP address assigned to it by LogMeIn (e.g., 25.x.x.x). An asterisk next to a host indicates that corresponding machine is currently online (Note: you will not see the machine your’re running the command from listed). Now that we have our Ubuntu server and our remote Linux client machine online, let’s see if we can initiate a terminal session with the server using SSH:
|
1 |
ssh <your-username>@<hamachi-IPaddress-for-your-ubuntu-server> |
You may receive a warning concerning the authenticity of the host you’re trying to reach along with a fingerprint of its public RSA key, and asked if you’re sure you want to continue connecting. If you’re absolutely sure that you are indeed connecting to your Ubuntu server, accept by typing yes and you’ll be presented with the login and password prompt. The public key from your Ubuntu server is stored in ~/.ssh/known_hosts. If you don’t want to have to remember the LogMeIn Hamachi IP address each time you want to run an SSH session with your server, simply add the IP address along with a name (e.g. home-server-ssh) to your hosts file (/etc/hosts). Next time you use LogMeIn Hamachi/SSH to connect to your server, use the name instead of the IP address and the host file will resolve the IP address for you.
Install and Configure LogMeIn Hamachi on a Windows Client
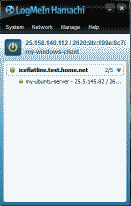
Configuring a Windows machine to access your Ubuntu server remotely is easy too. Download and install the Windows version of LogMeIn Hamachi. When you fire up the application for the first time, LogMeIn Hamachi will be in the offline state. Select the Power On icon on the top left of the application). A pop-up screen will appear asking you to enter the nickname to assign to your remote machine. After it is entered, the application will go online; however, we won’t see our Ubuntu server just yet, we first must add ourselves to the network we created. Select the “Join an existing network” and fill in the name of the network and the password you created when setting up the Ubuntu Server and select “Join”. You should see the name of the LogMeIn Hamachi network we created, as well the LogMeIn Hamachi IP address and nickname for our Ubuntu server appear in the screen (See Figure 1). Once installed, the LogMeIn Hamachi application will start whenever Windows starts and the user has logged in. You’ll find various configuration settings for the application under System->Preferences.
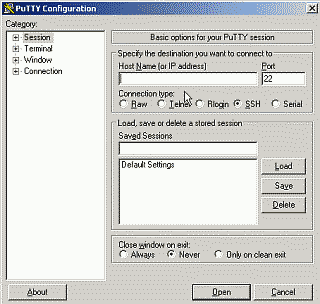
We’re almost there. Now we need to download and install an SSH application (Windows doesn’t support SSH natively). There are many out there to choose from, but the one I typically use is PuTTY, a free implementation of Telnet and SSH for Win32 and Linux/Unix platforms. Download PuTTY.exe (or the Installer version if you’d prefer) and run it. Enter the LogMeIn Hamachi IP address for your Ubuntu server in the Host name field, make sure to select the SSH radio button, and then select “Open” (See Figure 2).
You may receive a warning concerning the authenticity of the host you’re trying to reach along with a fingerprint of its public RSA key, and asked if you’re sure you want to continue connecting. If you’re absolutely sure that you are indeed connecting to your Ubuntu server, accept by selecting Yes; a terminal emulator will open and you’ll be presented with the login and password prompt.
If you don’t want to have to remember the LogMeIn Hamachi IP address each time you want to run a session with your server, then simply add the address along with a name of your choice (e.g. home-server-ssh) to your hosts file (/windows/system32/drivers/etc/hosts). Next time you use SSH to connect to your server, use the name instead of the IP address and the hosts file will resolve the IP address for you.
Additional Security
As you may have noticed, we’re using conventional password authentication in order to prove to our Ubuntu server who we claim to be. That may be an acceptable level of authentication considering we’re also authenticating over SSH and a secure VPN tunnel. However, you may want to have a more secure form of authentication. Public key authentication is an alternative means of identifying yourself to your Ubuntu server. Instead of typing a password, you generate a key pair, consisting of a public key (which your server is allowed to know) and a private key (which you keep secret and do not give out). The private key is able to generate signatures. A signature created using your private key cannot be forged by anybody who does not have that key; but anybody who has your public key can verify that a particular signature is genuine. Public key authentication is more secure and more flexible, but a little more difficult to set up. We’ll walk through the steps on both a Linux and a Windows client machine in the follow examples, but in essence what is involved is generating a key pair on our remote client machine, and copying the public key to the Ubuntu server. Then, when the server asks to prove who we are, the SSH application can generate a signature using your private key. The server can verify that signature (since it has your public key) and allow you to log in.
- Linux Client
Let’s set up our remote Linux client for public key authentication. We first need to generate the public/private key pair:
|
1 |
ssh-keygen –q –t rsa |
By default the RSA keys are 2048 bits. You can increase this to 4096 bits if desired with the -b option:
|
1 |
ssh-keygen –q –t rsa –b 4096 |
You’ll be asked by the script where it should store the keys (~/.ssh is the default), and then asked to enter in a passphrase in order to encrypt the private key that will be stored in this machine. If you don’t want to be asked for a passphrase each time you connect, just press enter. It is up to you to decide whether or not you should password encrypt your key when you create it. However, if you don’t, then anyone gaining access to your private key will automatically have SSH access to the server. After you enter a passphrase and confirm it, or simply hit enter, your encrypted private key (id_rsa) and your public key (id_rsa.pub) are generated and stored in ~/.ssh (assuming you accepted the default directory).
Now that our keys are generated, let’s move the public key to our Ubuntu server. Ensure that LogMeIn Hamachi is running, then enter the following command:
|
1 |
ssh-copy-id <your-username>@<logmein-hamachi-IP-address-for-your-ubuntu-server> |
This command will copy your public key to ~/.ssh/authorized_keys on your Ubuntu server. That’s it. Now, next time you use SSH/LogMeIn Hamachi to initiate a session with your server you’ll be asked to provide the passphrase (if you provided one when you generated the keys) for your private key instead of your server password. Congrats, you’re now using public key authentication to login to your server. Once you know your key pair works back up both the public and private keys files to an offline media, such as a USB flash drive or CD.
- Windows Client
Configuring our remote Windows client for public key authentication requires a little more work. First, we need a Windows application that can generate the public/private key pair. We’ll use PuTTYgen, PuTTY’s key generation utility, to perform this task. PuTTYgen is installed automatically if you use the Windows installer version of PuTTY, else you can simply download and use the standalone version of PuTTYgen.
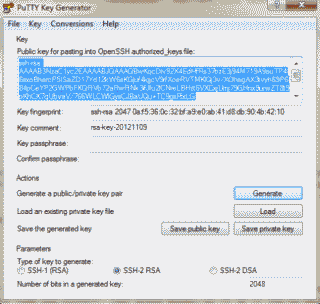
Start PuTTYgen and verify that “SSH-2 RSA” is selected and change the “Number of bits in a generated key” field to 2048 (or more). Select “Generate” where you’ll be asked by PuTTYgen to move your mouse over the applications blank area in order to generate “randomness.” PuTTYgen will then proceed to create your public/private key pair (See Figure 3).
You may now enter a passphrase for you private key and confirm it. Again, it’s up to you to decide whether or not to protect your private key with a passphrase. However, electing not to means that anyone gaining access to your private key will have SSH access to the server. You also have the opportunity to modify the “Key comment” field. The default entry is the key type and the date it was created. If you intend on creating additional keys, you may wish to populate this field with something different in order to help you differentiate between the various keys.
When complete, select “Save private key” and choose a file name and a location to save the *.ppk file. Next, carefully copy the text contained in the “Public key for pasting into OpenSSH authorized_keys file” box into a text file and save it. Using a program like WinSCP copy the text file to your user account on the Ubuntu server. Now, login to this account and append the contents of this text file to the file ~/.ssh/authorized_keys and make sure permissions are set correctly:
|
1 2 |
cat ~/<your-text-file> >> ~/.ssh/authorized_keys chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keys |
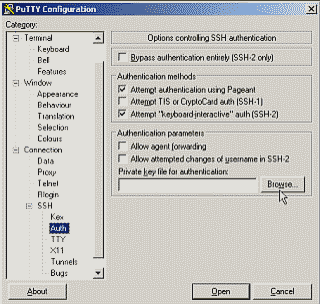
We’re done with PuTTYgen so let’s exit the program. Now fire up PuTTY and navigate to Connection->SSH->Auth. Under Authentication parameters select the Browse button and select the *.ppk file you saved in the previous step (See Figure 4). Now, navigate back up to Session and enter the LogMeIn Hamachi IP address for your server in the Host name field, make sure to select the SSH radio button, and then select Open (of course, LogMeIn Hamachi should be running). You may receive a warning concerning the authenticity of the host you’re trying to reach along with a fingerprint of its public RSA key, and asked if you’re sure you want to continue connecting. Accept by selecting Yes; you’ll be asked to provide the passphrase (if you created one) for your private key instead of your server password. Congrats, you’re now using public key authentication to login to your server. Once you know your key pair works back up both the public and private keys files to an offline media, such as a USB flash drive or CD.
Now that we have public key authentication set up, you may be wondering if you can still logon to the server without a private key? In other words, can you still use your server username and password? The answer is yes. However, that can be changed. After you’re sure that public key authentication is working on the remote machines you’ll be using to access your Ubuntu server, you may want to consider shutting down password authentication. To do that, logon on to your server and open the OpenSSH server’s config file (/etc/ssh/sshd_config). Look for the line #PasswordAuthentication yes and change it to PasswordAuthentication no (Make sure to uncomment the line). Then restart the SSH server with the following command:
|
1 |
sudo /etc/init.d/ssh restart |
Conclusion
Good times eh? Using some open source tools and LogMeIn Hamachi, we set up a secure VPN between remote Windows and Linux clients, and our Ubuntu server. And, we didn’t have to touch our home gateway/router. We also improved the security of the network by using public key authentication.
References
https://help.ubuntu.com/community/SSH/OpenSSH/Keys
http://the.earth.li/~sgtatham/putty/0.60/htmldoc/
http://www.openssh.com/
http://www.ibm.com/developerworks/library/l-keyc.html
Very nice article. This is exactly what I was trying to do as well. Thanks a bunch.
Michael, you’re very welcome. Thanks for your kind comment.
This is what I am looking for. Thakns a lot…. good job
Roman, Thanks! Glad it was helpful.
Thanks for this post, answers a bunch of questions I was having.
My pleasure Mark. Glad it was helpful for you.
Thanks alot! all the other guides didn’t work, but this one did :D
Regards
Donno, excellent! I’m glad it helped.
Very nicely described process for Hamachi setup.
This might be a silly question but I haven’t been able to find an answer anywhere:
I regularly use Hamachi with 3 M$ boxes and I want to add my linux box to that network. How do I login or link my linux box to that pre-existing account and network? Or do I need to go the opposite way and add my windows boxes to my network created using Linux?
I’ve read a couple instruction sets so far and can’t find any answer :-/
Just landed on this post via Google search. I love it. This situation switch my percept and I am taking the RSS feeds. Cheers Up.
Zander, my apologies for the delay in responding. My job has kept me pretty busy lately.
Your question isn’t silly at all. To bring your Linux box up on any Hamachi network just follow the steps described in the Configure a Remote Linux Client above.
So, first you would start Hamachi on your Linux box:
[plain light=”true”]
hamachi start
[/plain]
Then bring the Hamachi daemon online:
[plain light=”true”]
hamachi login
[/plain]
Create a nickname for your Linux box:
[plain light=”true”]
hamachi set-nick <nickname>
[/plain]
Then join the network you created for your MSFT hosts:
[plain light=”true”]
hamachi join <network> <password>
[/plain]
Finally, bring your Linux machine online on that network:
[plain light=”true”]
hamachi go-online <network>
[/plain]
That should do it. Then, the following commands will retrieve and display the nicknames of the hosts that are currently online. Note though that nickname of the host you’re issuing the commands from will not be displayed:
[plain light=”true”]
hamachi get-nicks && hamachi list
[/plain]
My pleasure Issac, and thank you.
Excellent how-to.
I have been looking for something like this for years (but am a Ubuntu/Linux newby)
I did have a little trouble though.
With my Ubuntu/Windows setup I followed the instructions but kept getting
bash: .ssh/authorized_keys: No such file or directory
when I tried to run the
cat id_rsa.pub >> .ssh/authorized_keys
and
chmod 700 .ssh && chmod 600 .ssh/authorized_keys
steps.
I tried many things but only the following worked (because it is the last thing I tried)
cat id_rsa.pub >> ~/.ssh/authorized_keys
and then
chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keys
I don’t know why I had to prepend the home folder (~/) before the files, as I was in the home folder, but this works.
iceflatline, if this is stepping on your shoes please delete my comment but if you could append the how to, I think other newbies might find this information useful.
I figured how to do do the steps from this website http://www.askflib.com/article/generating-and-using-rsa-ssh-keys
Hi, I’m on day 3 ubuntu so be gentle on me. :-) I followed through to here
chmod +x hamachi && sudo mv hamachi/etc/init.d/
but i get an error
mv: missing destination file operand after `hamachi/etc/init.d/’
in my i have a folder “hamachi” and inside that a file “hamachi” which has your script .
I tried copy and pasting it to the etc/init.d folder but of course linux was having none of that kind of stuff and blocked on permissions :-)
any help appreciated
Aud, thank you for your comment. Good catch.
In a previous step in the article I showed how to transfer a public key from a Linux client to the Ubuntu server using the ssh-copy-id command. This would have created ~/.ssh/authorized_keys on the server and the command would have worked. However, if you skipped that step (which would make sense to do if you were interested in only setting up a Windows client…), the authorized_keys file would not already be there, resulting in the error you encountered. Using the absolute path in the command forces cat to create the file if it does not already exist.
This was sloppy writing on my part and a good reminder to use absolute paths in commands in my articles going forward.
I have revised the article to include the absolute path to the file per your suggestion.
Thanks again for your contribution!
Saul, thank you. My bad; the command in the article was missing a space.
Make sure there is a space between hamachi and /etc/init.d/ in the command.
Thanks for catching this.
Fantastic how-to. Saved me hours!
A quick question about the start-up script. I seem to need the additional command:
hamachi go-online
after rebooting my server. Should this be added to the script? Or is there something I’m missing in my setup?
I meant the command:
hamachi go-online [networkname]
But having thought about it, I wonder if this is because I created my network online at logmein.com? If I’d done it as you instruct — all from Ubuntu — then maybe this would not be needed?
Also, does anyone happen know if Hamachi always finds the fastest peer-to-peer route? I’m often on the same local LAN as my Ubuntu server. So I’m wondering if there’s a speed hit going via Hamachi? I don’t seem to notice much difference so far.
Again, a really useful how-to, so thanks!
Joe, hi, and thanks for your comments. The short answer is no. Once the Hamachi network is created/joined, the nickname established, and the server added with the go-online command, the script will start tuncfg and then start Hamachi. You should then be back online with out the extra command.
I’m not familiar enough with Logmein’s online creation system enough to know if that caused you problems or not.
Fantastic job mate, using this primer I could make it *EASILY* to configure my Windows 7 client in a snap, to use both Putty and Netbeans enabling remote server file transfer (Linux) using SFTP/SSH.
By the way, is it better to use RSA or DSA keys?
Thanks again
Arno, thanks for your kind comments. I’m glad the article worked well for you. Regarding DSA versus RSA keys, even though these two key signing algorithms were state of the art when SSH was invented, The DSA key signing algorithm has apparently come to be seen as less secure over the years. According to PuTTY’s author for example: “DSA has an intrinsic weakness which makes it very easy to create a signature which contains enough information to give away the private key!” However, others, including RSA, seem to dismiss the concerns. My sense? Notwithstanding the need to support SSH-1 protocol (RSA is your only choice), both are probably more than adequate for the average home network application using SSH such as the one described in this article. By the way, for a really good article on OpenSSH key management, check out this one written for IBM in 2001 by Daniel Robbins, President and CEO, Gentoo Technologies, Inc.
thx iceflatline. thx to you I have implemented it successfully for my file server (linux samba server with windows 7 client) . I have a question though.
I am also trying to access an application on the same server which i locally access over http://192.168.1.x:8088/admin. When i replace the 192.168.1..x with the hamachi ip address it doesn’t work. Would you able to point me in a direction to solve the problem?
The application is a server implementation of Adempiere (an ERP solution).
thx in advance
phil, thanks for your comment and question. I’m not familiar with Adempiere, but assuming you can reach the Samba server through Hamachi and can reach the URL locally, I would check to see if your implementation’s web server is accepting connections on your local interface only. Occasionally, on Apache for example, I have had to add a “Listen” directive to point to another interface:
[text light=”true”]
Listen 192.168.1.x:80
Listen <the hamachi address>:8080
[/text]
Just a thought…
Outstandingly amazing article. I will try to set up exactly this thing today. Happy that I stumbled upon your blog!
Thanks for sharing!
Stefanos, thanks for your kind comments.
Wow! Excellent article, thanks so much. Helped answer all my questions.
Aaron, my pleasure. Glad you enjoyed it.
Works perfect on my Ubuntu natty 11.04 server.
Thanks a lot, have been trough a few other howtos but nothing as complete as this one.
Only installation of Hamachi i did differently
sudo wget https://secure.logmein.com/labs/logmein-hamachi_2.0.1.15-1_i386.deb
sudo dpkg -i logmein-hamachi_2.0.1.15-1_i386.deb
or on a 64 bit:
sudo wget https://secure.logmein.com/labs/logmein-hamachi_2.0.1.15-1_amd64.deb
sudo dpkg -i logmein-hamachi_2.0.1.15-1_amd64.deb
Erik van Berkum
Erik, thanks so much for passing along this information (and for your kind words).
Thanks for the great guide, iceflatline. It works for me in my home LAN. However, I’m having some issues connecting to my home Ubuntu 10.04 server remotely from my work laptop (Windows 7)using this method. The Ubuntu server is unreachable and cannot be pinged (reply times out). I thought it may be a work firewall issue, but using the same Windows Hamachi client specified in this guide on a Windows 7 machine at home I am able to get at least a “relayed” connection. I think it has to do with the Ubuntu Server’s DHCP configuration. Any thoughts?
Sorry I forgot to add that my home LAN consists of a switch connecting all my devices which is then uplinked to a router/switch device connected to a cable modem. All devices belong to the same subnet so the extra switch is transparent(well should be!). Probably why I get only a relayed connection.
Thanks for this i will try this as soon as possible, the classic VPN failed bcs i can’t modify the firewall on both sides, n2n failed too so i’ll try this. Is it fast enough to transfer files over ssh? Thansk a lot!
Godwin, thanks for the comments. Is the small star next the Ubuntu server’s nick in your Hamachi client in Windows green?
chaeMil, so long as your connection is reasonably fast it should be.
You’re welcome, iceflatline. It’s yellow.
Godwin, from time to time I’ve also had issues connecting to my Ubuntu server, depending on the network I’m trying to connect from. I suspect this might be an issue with LogMeIn’s mediation server used to track static IP allocations and nicks for Hamachi. By chance, have you tried to connect from a different network?
I’ve not had the chance to try connecting from a different network. I’ll give that a go!
By the way, thank you for your helpful responses.
This tutorial is really excellent. Thanks for posting! Also, as a blog owner myself, I really like what you have here.
suBDavis, you’re very welcome. Thanks for the kind words.
Excellent ! ! !
Thanks!
thx. first tut that works for me. but ive gotta ununtu desktop with text-mode boot as standard, but when i do sudo /etc/init.d/lightdm start lightDM starts but putty still logs on without desktop (needing xming or so). So, can i access desktop via putty to? else i would start teamviewer via putty after starting lightdm, but it would be nicer without.
MrBlack, sorry, based on your description, I’m not clear what you’re trying to do.
Its really helpful
[…] Remote Access To Your Ubuntu Server Using PuTTY, Hamachi … – 45 Responses to “Remote Access To Your Ubuntu Server Using PuTTY, Hamachi and SSH” Michael Smith Says: December 9th, 2009 at 6:36 pm. Very nice article…. […]
[…] Remote Access To Your Ubuntu Server Using PuTTY, Hamachi and SSH hamachivpn 0 commenti […]
Hi,
I have setted all this in my ubuntu server and in my windows, from the windows, I can access to the server by typping ssh ubuntu_user_name@hamachi_ip, but I can’t access to the windows from the ubuntu server, could you help me with this?
Santiago, thank you for your comment. It has been many years since I have used Hamachi on either Linux or Windows so I am not sure how much help I can provide. If I understand your message correctly, you are unable to ssh from the Ubuntu system to the Windows system. I have not tried to do that before, but I would suggest you start by checking that the SSH server you are running in Windows is properly configured. For example, perhaps it’s listening on a port other than the default 22. You might also check whether Window’s internal firewall is correctly configured to pass traffic to the SSH server. Good luck.